Source Code Audit
INTRODUCTION
APPROACH
Our Approach to Ransomware Aeadiness Assessment
Our approach to Selkey Cyber Security’s Source Code Audit emphasizes integrating security seamlessly into Agile Methodology, enabling the development of highly secure applications through accurate, exhaustive, and cost-effective code analysis.
In today’s digital landscape, where enterprises face constant threats from malicious attacks, source code analysis emerges as a critical priority. It becomes imperative for organizations to review both internally developed and third-party software rigorously before deployment, ensuring the identification and remediation of vulnerabilities.
Selkey Cyber Security’s approach to source code analysis combines extensive market research with predefined security principles to identify security bugs within the source code. These predefined principles assist enterprises in detecting common programming flaws such as anti-patterns, logic errors, memory leaks, and workflow flaws. Additionally, Selkey Cyber Security utilizes Static Application Security Testing (SAST) automated tools to scan application code for vulnerabilities while it is in a static or non-running state. This proactive approach enables developers to remediate issues early in the Software Development Life Cycle (SDLC), enhancing the overall security posture of the application.
By integrating security seamlessly into Agile Methodology and leveraging a combination of market research, predefined principles, and automated tools, Selkey Cyber Security ensures that source code analysis is conducted comprehensively and effectively, resulting in the development of highly secure applications.
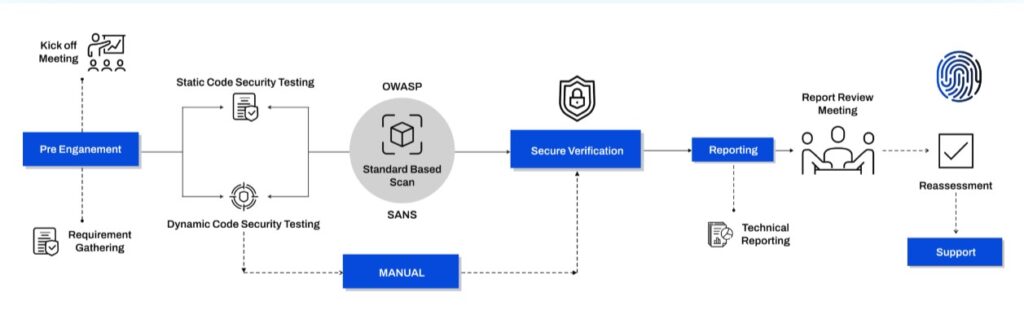
Methodology
In our methodology, we adhere strictly to your rules to ensure a comprehensive and effective approach to identifying technical vulnerabilities.
