AWS Penetration Testing

RISK
Amazon Web Services (AWS) stands as the leading cloud platform, serving over a million users across 190 countries. It offers a diverse array of services, including scalable computing, cloud storage, databases, data analytics, AI applications, and tools for deployment and automation.
While AWS has removed many burdens, such as the need for on-premise data centers, distributed computing systems, and hardware management, it has not eliminated cybersecurity risks. Penetration testing is an effective strategy for uncovering security vulnerabilities in a cloud environment. A penetration tester can identify critical security flaws in an AWS setup and provide practical recommendations to address them.
Protect your AWS infrastructure!
Frameworks, PaaS, IaaS, and SaaS are designed to be both secure and customizable for users. However, some aspects are not simply plug-and-play services.
Is AWS Secure?
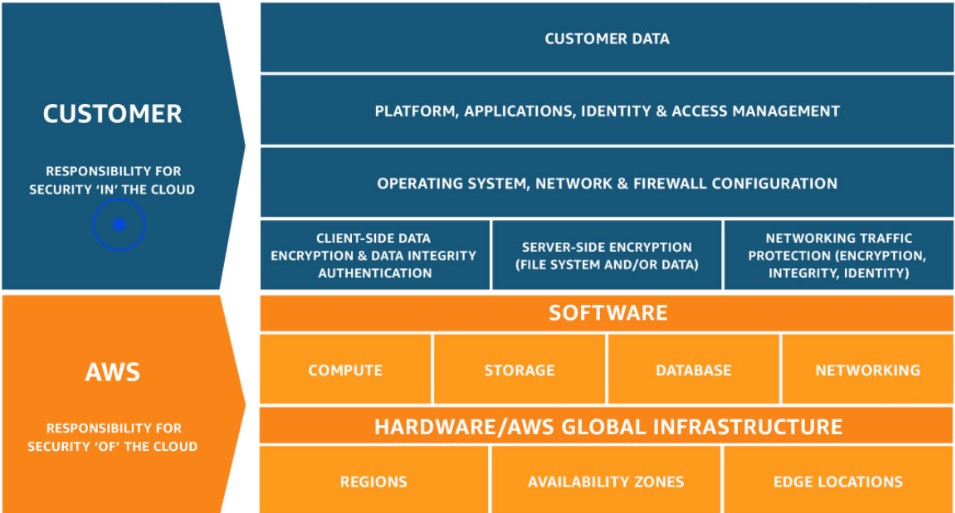
Understanding the Shared Responsibility Model
Security evaluation within AWS operates under the framework of the shared responsibility model, which delineates between two essential security domains:
1. Security of the Cloud: This encompasses the protection of the AWS cloud infrastructure itself, along with all associated services. Amazon takes charge of securing this aspect and routinely conducts security assessments, both internally and externally. However, customers are not granted permission to conduct penetration testing on AWS’s cloud infrastructure.
2. Security in the Cloud: This pertains to the security of the assets and resources that organizations deploy on the AWS platform. It is the responsibility of the respective companies to ensure the security of their applications, assets, and systems. While Amazon doesn’t allow penetration testing on its cloud infrastructure, organizations are encouraged to conduct such tests to verify the security of their deployments.
Approach & Methodology
Penetration testing in AWS should prioritize examining assets owned by users, evaluating access management, configuring user permissions, and assessing the utilization of AWS APIs integrated deeply within the AWS environment. This involves targeting and compromising AWS IAM Keys, testing S3 bucket configuration and permission vulnerabilities, establishing access via Lambda backdoor functions, and obscuring tracks by manipulating CloudTrail logs. These strategies are tailored to AWS Cloud and necessitate specific expertise and methodologies.
